- Cisco Anyconnect Keychain Login
- Cisco Anyconnect Vpn Software Download
- Cisco Anyconnect Keychain Windows 10
- Cisco Anyconnect Windows 10
- Cisco Anyconnect Keychain Download
- Cisco Anyconnect Secure Mobility Client Keychain
- Cisco Anyconnect Keychain Login
Yosemite 10.10.3 & Cisco AnyConnect Secure Mobility Client version 3.1.07021. OS X wants to make changes. Type an administrator's name and password to allow this. OS X wants to use the 'System' keychain. Open Keychain Access Select ‘System’ which can be found in the menu displayed on the left hand side Find “com.apple.kerberos.kdc” certificate and public key (there should be two duplicates of each of them). #!/usr/bin/env python # # This script will launch the Cisco AnyConnect Mobility Client from the # command line, and using credentials stored in the the user's Logon Keychain. This is to cover cases where the AnyConnect client attempts to collect user certificates from the keychain despite not needing to per the ASA setup. How to enable Certificate Matching: Log in to your Cisco Adaptive Security Device Manager (ASDM). Click the Configuration tab. In the left menu, click Remote Access VPN.
MobiLock and Android for Work makes it easy for you to configure Cisco AnyConnect VPN on your managed Android devices. Follow the guide below to configure Cisco AnyConnect.
Before you Begin
- Complete Android for Work Setup in MobiLock Dashboard.
- Enroll your corporate owned devices using afw#mobilock
- Invite your Employees to enroll their Personal devices.
Search and Approve Cisco AnyConnect
The first step is to search and approve Cisco AnyConnect for your organization. The steps are,
- Sign In MobiLock Dashboard.
- Navigate to Enterprise > My Apps > Play For Work Apps
- Click on SEARCH&ADD button to see the Google Play dialog.
- In the Google Play dialog search for Cisco AnyConnect,
- Click on the Cisco AnyConnect app and select Approve
- Follow the onscreen instructions to approve the application. Click Done to close the dialog and now the app starts appearing on the MobiLock Dashboard.
Configuring Cisco AnyConnect Settings
Once you have the AnyConnect app, the next step is to configure the application. The steps are,
- Click on the AnyConnect application to see the details card.
- Click on the App Configurations tab and click CREATE to see the configuration options.
- Cisco AnyConnect gives you the following configuration options,
Connection Name
The display name for the VPN as shown on user's mobile device
Host
The URL of the headend that is the actual Cisco VPN Server.
Protocol
Choose between SSL or IPSec.
IPSec Authentication Mode
If the selected protocol is IPSec, then choose the authentication mode.
IKE Identity
Optional field to specify the data on how to identify a user connection.
Keychain Certificate Alias
KeyChain alias of the client certificate to use for this VPN configuration.
Per App VPN Allowed Apps
Deprecated. Use the setting below
Per App VPN Allowed Apps
Specify a comma separated list of applications that should be routed through VPN.
Per App VPN Disallowed Apps
Specify a comma separated list of applications that should not be routed through VPN.
Allow Apps to Bypass VPN Tunnel
Choose if you want the applications to bypass the VPN Tunnel.
Set Active
Select this to make the default selected VPN Configuration.
FIPS Mode
Select to enable FIPS mode for AnyConnect.
Certificate Revocation
AnyConnect Profile
Enter the AnyConnect Profile in XML format.
Device Identifier
Enter the device identifier that should be reported to VPN Server.
Report Hardware Identifiers for VPN Identification
Enable if the H/W identifiers like Mac and/or IMEI should be reported to VPN Server.
Allow Users to Save Credentials
Choose if user can save the VPN Credentials so that they are not asked for it repeatedly.
- Once you have entered the values, click on SAVE to save the configuration. All the saved configuration appear in the list.
Cisco Anyconnect Keychain Login
Publishing the Application and Configuration
Once you have created the configuration, the next step is to publish the application and then the configuration. The steps are,
- From the App Details card, click on the App Information tab and click on PUBLISH
- Select the Android Device Groups/Profiles/Devices where you want to publish the application and click PUBLISH
- Now click on the App Configuration tab. Click on the Publish icon.
- Select the Android Device Groups/Profiles/Devices where you have published the application in Step 3, and click PUBLISH
- This will cause the applications to be installed on the devices and then configured based on the configuration.
How did we do?
Related Articles
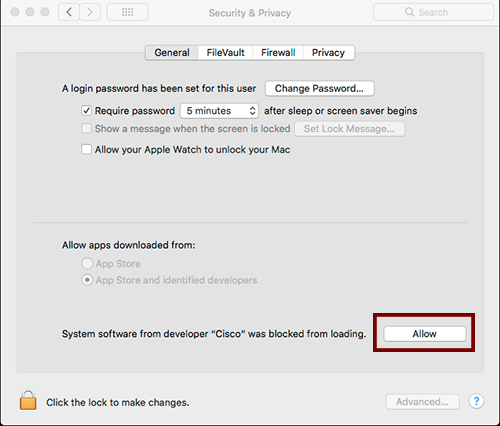
Cisco Anyconnect Vpn Software Download
Contributions to OpenConnect are very welcome. You don't need to be able to writecode. Testing, documentation improvements and especially translations are allextremely useful. Some specific suggestions and requests for help can be found below.
Submitting Patches
Patches can be sent to the mailing list or directly to the author in private email. We are also experimentingwith using GitLab, so please feel free to file issues and submit merge requests athttps://gitlab.com/openconnect/openconnect.
When submitting patches to be included in OpenConnect, please certify that yourpatch meets the criteria below by including include a sign-offline in your email which looks like this:
Signed-off-by: Random J Developer <random@developer.example.org>This confirms that you are permitted to submit the patch for inclusion in OpenConnect under the LGPLv2.1 licence. The full text of the certificate is as follows:
Developer's Certificate of Origin 1.1
By making a contribution to this project, I certify that:
- The contribution was created in whole or in part by me and I have the right to submit it under the open source license indicated in the file; or
- The contribution is based upon previous work that, to the best of my knowledge, is covered under an appropriate open source license and I have the right under that license to submit that work with modifications, whether created in whole or in part by me, under the same open source license (unless I am permitted to submit under a different license), as indicated in the file; or
- The contribution was provided directly to me by some other person who certified (1), (2) or (3) and I have not modified it.
and also that:
- I understand and agree that this project and the contributionare public and that a record of the contribution (including allpersonal information I submit with it, including my sign-off) ismaintained indefinitely and may be redistributed consistent withthis project or the open source license(s) involved.
Translations
One of the main things needed at the present time is translations intolanguages other than English. All contributions will be gratefully received.
Translations for OpenConnect are maintained in the GNOMENetworkManager-openconnect module.Translations can be contributed by joining the GNOME team as described on theirTranslationProjectwiki page, or simply by editing one of the language files in the po/directory and sending the resulting patch (or file) to the mailing list.
If there are questions about the messages because the intent is not clear, or if themessages could be improved to make translation easier or better, please also feel free toask or make suggestions on the mailing list.
Documentation / Web Site
OpenConnect is designed with the principle that 'if it needs documenting, fix it instead'. That isn'tto say that we don't have documentation. But if a user finds something non-obvious and has to look it upin the documentation, then that in itself is a little bit of a usability failure. Software should Just Work™.
So if you find something that is more complex than it needs to be, and you think it shouldJust Work™ then please don't hesistate totell usbout it.
Any improvements to the documentation are most welcome. In particular:
- Update web site to be mobile-friendly
The current template is definitely showing its age, and could very much do with an overhaul.
Cisco Anyconnect Keychain Windows 10
Testing
All testing is valuable, and please do let us know if anything doesn't work when you thinkit should. There are some things which the regular developers don't have easy access to test,some help with testing these would be particularly welcome:
Cisco Anyconnect Windows 10
- Testing a PAN GlobalProtect VPN with IPv6 internal addresses.
We think we know how this works, but we've not been able to test. - Various authentication methods for Pulse Secure.
Although it looked sane at first, the Pulse protocol has a lot of horrid special cases. Aside from the Host Checker most should be working, but please test and let us know if anything is missing or wrong.
Cisco Anyconnect Keychain Download
New Protocols
Cisco Anyconnect Secure Mobility Client Keychain
There are some other protocols which would be good to add to OpenConnect. Getting a newprotocol to the point where it basically works to send and receive traffic is only afew hours of work, and can be very rewarding.
For some protocols we already know how they work on the wire and it's mostlyjust a matter of typing. For others we might have to observe the existing clientsto learn how they work.
These would be great projects for someone to take on as a learning exercise, orperhaps even Google Summer of Code projects.
- CheckPoint VPN
This is an IPSec-based VPN with fallback to using the SSL transport. Some discussion of OpenConnect support in this GitLab ticket. - Cisco / Nortel IPSec VPN
These IPSec-based protocols are already supported by vpnc to differing extents, but vpnc is no longer actively maintained. Since OpenConnect now has ESP support, and since some of these protocols also fall back to operating over TCP when UDP and native ESP aren't available, it may make sense to implement them in OpenConnect now.
Suggestions for other protocols which OpenConnect could usefully implement, are also welcome.
Other enhancements
One of the main other improvements that would be welcome, is implementing a full WebView in the graphical clients. Currently for protocols like Juniper, OpenConnect screen-scrapes the HTML pages used for login, and attempts to make sense of them. This is The main thing that would be Other items on the TODO list include:Cisco Anyconnect Keychain Login
- WebView support in graphical clients.
OpenConnect currently screen-scrapes the HTML login pages for protocols like Juniper, which is fragile and error-prone. It would be great if the graphical interfaces like NetworkManager could use a real WebView to show the pages, which would work with JavaScript and various other customisations that the admins often make. This might make an excellent Google Summer of Code project, or would also suit someone just trying to contribute in their spare time. - Better support for running or emulating the 'Cisco Secure Desktop' trojan.
The Cisco hostscan tool seems to download and interpret a manifest file from the server and send back results based on the 'questions' therein. A native implementation of this would be useful. - GUI for OS X, perhaps based on Tunnelblick.
- Full Android keystore support.
OpenConnect's support for the Android keystore predates the Android keystore actually doing anything useful. We assume we can just ask for the private key and be given it. A real keystore would only allow us to perform signature operations using the key, and wouldn't just give it to us. Modern versions of Android can support this, and we should add support for it. - Mac OS X keychain support.
Likewise, using keys stored in the OS X keychain would be extremely useful.
