- Cisco AnyConnect Secure Mobility Client Administrator Guide ...
- Cisco Anyconnect Always On Vpn Download
- Cisco Anyconnect Always On Vpn Android
- Cisco Anyconnect Always On Vpn
- How To Configure Cisco SSL VPN AnyConnect Secure Mobility ...
- Cisco Anyconnect Windows Always On Vpn
tocIf you need to access resources that are only available on the UNT Network, you'll need to use Cisco VPN. To enable VPN, you may need to install a VPN client. If you're on a UNT-managed, Windows computer, you may already be using Always On VPN.UNT VPN connections will last a maximum of 24 hours before they will need to be reconnected (this is for security purposes).As. Although AnyConnect is always-on, it is also flexible enough to apply different policies base d on location, allowing users access to. Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. Always-on-vpn profile-setting. Anyconnect will try to use DTLS (TLS over UDP) whenever it is supported and not blocked by packetfilters on the way. In case it is notsupported or filtered, anyconnect will try to fallback to TLS over TCP. VPN over TCP has the disadvantage, that it may slow down tunneld TCP connections. For details have a look here. If you connect via the Cisco AnyConnect VPN client, you will need to type the new “sslvpn.asu.edu/2fa” address into the field, like below, before clicking on “Connect”. To use SSLVPN to have a dedicated tunnel for all traffic from you laptop back through the ASU SSLVPN, for example in the special case you are traveling in China, use.
Objective
The objective of this document is to show you how to configure AnyConnect VPN connectivity on the RV34x Series Router.
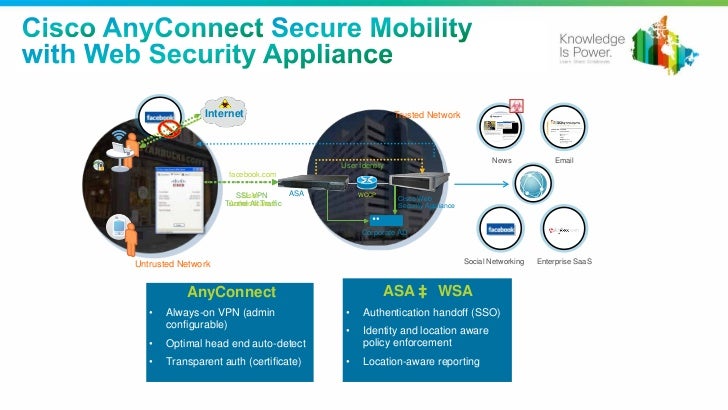
Advantages of using AnyConnect Secure Mobility Client:
- Secure and persistent connectivity
- Persistent security and policy enforcement
- Deployable from the Adaptive Security Appliance (ASA) or from Enterprise Software Deployment Systems
- Customizable and translatable
- Easily configured
- Supports both Internet Protocol Security (IPSec) and Secure Sockets Layer (SSL)
- Supports Internet Key Exchange version 2.0 (IKEv2.0) protocol
Introduction
A Virtual Private Network (VPN) connection allows users to access, send, and receive data to and from a private network by means of going through a public or shared network such as the Internet but still ensuring secure connections to an underlying network infrastructure to protect the private network and its resources.
A VPN client is software that is installed and ran on a computer that wishes to connect to the remote network. This client software must be set up with the same configuration as that of the VPN server such as the IP address and authentication information. This authentication information includes the username and the pre-shared key that will be used to encrypt the data. Depending on the physical location of the networks to be connected, a VPN client can also be a hardware device. This usually happens if the VPN connection is used to connect two networks that are in separate locations.
The Cisco AnyConnect Secure Mobility Client is a software application for connecting to a VPN that works on various operating systems and hardware configurations. This software application makes it possible for remote resources of another network become accessible as if the user is directly connected to his network, but in a secure way. Cisco AnyConnect Secure Mobility Client provides an innovative new way to protect mobile users on computer-based or smart-phone platforms, providing a more seamless, always-protected experience for end users and comprehensive policy enforcement for IT administrator.
On the RV34x router, starting with firmware version 1.0.3.15 and moving forward, AnyConnect licensing is not necessary. There will be a charge for client licenses only.
For additional information on AnyConnect licensing on the RV340 series routers, please see the article on: AnyConnect Licensing for the RV340 Series Routers.
Applicable Devices | Firmware Version
- Cisco AnyConnect Secure Mobility Client | 4.4 (Download latest)
- RV34x Series | 1.0.03.15 (Download latest)
Configure AnyConnect VPN Connectivity on the RV34x
Configure SSL VPN on the RV34x
Step 1. Access the router web-based utility and choose VPN > SSL VPN.
Step 2. Click the On radio button to enable Cisco SSL VPN Server.
Mandatory Gateway Settings
The following configuration settings are mandatory:
Cisco AnyConnect Secure Mobility Client Administrator Guide ...
Step 3. Choose the Gateway Interface from the drop-down list. This will be the port that will be used for passing traffic through the SSL VPN Tunnels. The options are:
- WAN1
- WAN2
- USB1
- USB2
Note: In this example, WAN1 is chosen.
Step 4. Enter the port number that is used for the SSL VPN gateway in the Gateway Port field ranging from 1 to 65535.
Note: In this example, 8443 is used as the port number.
Step 5. Choose the Certificate File from the drop-down list. This certificate authenticates users who attempt to access the network resource through the SSL VPN tunnels. The drop-down list contains a default certificate and the certificates that are imported.
Note: In this example, Default is chosen.
Step 6. Enter the IP address of the client address pool in the Client Address Pool field. This pool will be the range of IP addresses that will be allocated to remote VPN clients.
Note: Make sure that the IP address range does not overlap with any of the IP addresses on the local network.
Note: In this example, 192.168.0.0 is used.
Step 7. Choose the Client Netmask from the drop-down list.
Note: In this example, 255.255.255.128 is chosen.
Step 8. Enter the client domain name in the Client Domain field. This will be the domain name that should be pushed to SSL VPN clients.
Note: In this example, WideDomain.com is used as the client domain name.
Step 9. Enter the text that would appear as login banner in the Login Banner field. This will be the banner that will be displayed each time a client logs in.
Note: In this example, Welcome to Widedomain! is used as the Login Banner.
Optional Gateway Settings
The following configuration settings are optional:
Step 1. Enter a value in seconds for the Idle Timeout ranging from 60 to 86400. This will be the time duration that the SSL VPN session can remain idle.
Note: In this example, 3000 is used.
Step 2. Enter a value in seconds in the Session Timeout field. This is the time it takes for the Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) session to time out after the specified idle time. The range is from 60 to 1209600.
Note: In this example, 60 is used.
Step 3. Enter a value in seconds in the ClientDPD Timeout field ranging from 0 to 3600. This value specifies the periodic sending of HELLO/ACK messages to check the status of the VPN tunnel.
Note: This feature must be enabled on both ends of the VPN tunnel.
Note: In this example, 350 is used.
Step 4. Enter a value in seconds in the GatewayDPD Timeout field ranging from 0 to 3600. This value specifies the periodic sending of HELLO/ACK messages to check the status of the VPN tunnel.
Note: This feature must be enabled on both ends of the VPN tunnel.
Note: In this example, 360 is used.
Step 5. Enter a value in seconds in the Keep Alive field ranging from 0 to 600. This feature ensures that your router is always connected to the Internet. It will attempt to re-establish the VPN connection if it is dropped.
Note: In this example, 40 is used.
Step 6. Enter a value in seconds for the duration of the tunnel to be connected in the Lease Duration field. The range is from 600 to 1209600.
Note: In this example, 43500 is used.
Step 7. Enter the packet size in bytes that can be sent over the network. The range is from 576 to 1406.
Note: In this example, 1406 is used.

Step 8. Enter the relay interval time in the Rekey Interval field. The Rekey feature allows the SSL keys to renegotiate after the session has been established. The range is from 0 to 43200.
Note: In this example, 3600 is used.
Step 9. Click Apply.
Configure Group Policies
Step 1. Click the Group Policies tab.
Step 2. Click the Add button under the SSL VPN Group Table to add a group policy.
Note: The SSL VPN Group table will show the list of group policies on the device. You can also edit the first group policy on the list, which is named SSLVPNDefaultPolicy. This is the default policy supplied by the device.
Step 3. Enter your preferred policy name in the Policy Name field.
Note: In this example, Group 1 Policy is used.
Step 4. Enter the IP address of the Primary DNS in the field provided. By default, this IP address is already supplied.
Note: In this example, 192.168.1.1 is used.
Step 5. (Optional) Enter the IP address of the Secondary DNS in the field provided. This will serve as a backup in case the primary DNS failed.
Note: In this example, 192.168.1.2 is used.
Step 6. (Optional) Enter the IP address of the primary WINS in the field provided.
Note: In this example, 192.168.1.1 is used.
Step 7. (Optional) Enter the IP address of the secondary WINS in the field provided.
Note: In this example, 192.168.1.2 is used.
Step 8. (Optional) Enter a description of the policy in the Description field.
Note: In this example, Group Policy with split tunnel is used.
Step 9. (Optional) Click on a radio button to choose the IE Proxy Policy to enable Microsoft Internet Explorer (MSIE) proxy settings to establish VPN tunnel. The options are:
- None - Allows the browser to use no proxy settings.
- Auto - Allows the browser to automatically detect the proxy settings.
- Bypass-local - Allows the browser to bypass the proxy settings that are configured on the remote user.
- Disabled - Disables the MSIE proxy settings.
Note: In this example, Disabled is chosen. This is the default setting.
Step 10. (Optional) In the Split Tunneling Settings area, check the Enable Split Tunneling check box to allow Internet destined traffic to be sent unencrypted directly to the Internet. Full Tunneling sends all traffic to the end device where it is then routed to destination resources, eliminating the corporate network from the path for web access.
Step 11. (Optional) Click on a radio button to choose whether to include or exclude traffic when applying the split tunneling.
Note: In this example, Include Traffic is chosen.
Step 12. In the Split Network Table, click the Add button to add split Network exception.
Step 13. Enter the IP address of the network in the field provided.
Note: In this example, 192.168.1.0 is used.
Step 14. In the Split DNS Table, click the Add button to add split DNS exception.
Step 15. Enter the Domain name in the field provided and then click Apply.
Verify AnyConnect VPN Connectivity
Step 1. Click on the AnyConnect Secure Mobility Client icon.
Step 2. In the AnyConnect Secure Mobility Client window, enter the gateway IP address and the gateway port number separated by a colon (:), and then click Connect.
Note: In this example, 10.10.10.1:8443 is used. The software will now show that it is contacting the remote network.
Step 3. Enter your server username and password in the respective fields and then click OK.
Note: In this example, Group1 user is used as the Username.
Step 4. As soon as the connection is established, the Login Banner will appear. Click Accept.
The AnyConnect window should now indicate the successful VPN connection to the network.
Step 5. (Optional) To disconnect from the network, click Disconnect.
You should now have successfully configured AnyConnect VPN connectivity using an RV34x Series Router.
View a video related to this article...
Introduction
This document describes the Cisco AnyConnect Mobility Client captive portal detection feature and the requirements for it to function correctly. Many wireless hotspots at hotels, restaurants, airports, and other public places use captive portals in order to block user access to the Internet. They redirect HTTP requests to their own websites that require users to enter their credentials or acknowledge terms and conditions of the hotspot host.
Prerequisites
Requirements

Cisco recommends that you have knowledge of the Cisco AnyConnect Secure Mobility Client.
Components Used
The information in this document is based on these software versions:
- AnyConnect Version 3.1.04072
- Cisco Adaptive Security Appliance (ASA) Version 9.1.2
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
Many facilities that offer Wi-Fi and wired access, such as airports, coffee shops, and hotels, require users to pay before they obtain access, agree to abide by an acceptable use policy, or both. These facilities use a technique called captive portal in order to prevent applications from connecting until users open a browser and accept the conditions for access.
Captive Portal Remediation Requirements
Support for both captive portal detection and remediation requires one of these licenses:
Cisco Anyconnect Always On Vpn Download
- AnyConnect Premium (Secure Sockets Layer (SSL) VPN Edition)
- Cisco AnyConnect Secure Mobility
You can use a Cisco AnyConnect Secure Mobility license in order to provide support for captive portal detection and remediation in combination with either an AnyConnect Essentials or an AnyConnect Premium license.
Note: Captive portal detection and remediation is supported on the Microsoft Windows and Macintosh OS X operating systems supported by the release of AnyConnect that is in use.
Captive Portal Hotspot Detection
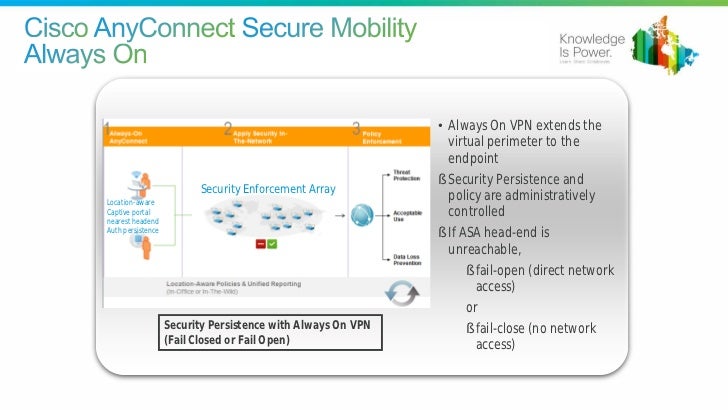
AnyConnect displays the Unable to contact VPN server message on the GUI if it cannot connect, regardless of the cause. The VPN server specifies the secure gateway. If Always-on is enabled and a captive portal is not present, the client continues to attempt to connect to the VPN and updates the status message accordingly.
If the Always-on VPN is enabled, the connect failure policy is closed, captive portal remediation is disabled, and AnyConnect detects the presence of a captive portal, then the AnyConnect GUI displays this message once per connection and once per reconnect:
If AnyConnect detects the presence of a captive portal and the AnyConnect configuration differs from that previously described, the AnyConnect GUI displays this message once per connection and once per reconnect:
Caution: Captive portal detection is enabled by default and is nonconfigurable. AnyConnect does not modify any browser configuration settings during captive portal detection.
Captive Portal Hotspot Remediation
Captive portal remediation is the process where you satisfy the requirements of a captive portal hotspot in order to obtain network access.
AnyConnect does not remediate the captive portal; it relies on the end user to perform the remediation.
In order to perform the captive portal remediation, the end user meets the requirements of the hotspot provider. These requirements might include payment of a fee to access the network, a signature on an acceptable use policy, both, or some other requirement that is defined by the provider.
Captive portal remediation must be explicitly allowed in an AnyConnect VPN Client profile if AnyConnect Always-on is enabled and the Connect failure policy is set to Closed. If Always-on is enabled and the Connect Failure policy is set to Open, you do not need to explicitly allow captive portal remediation in an AnyConnect VPN Client profile because the user is not restricted from network access.
False Captive Portal Detection
AnyConnect can falsely assume it is in a captive portal in these situations.
- If AnyConnect attempts to contact an ASA with a certificate that contains an incorrect server name (CN), then the AnyConnect client will think it is in a captive portal environment.
In order to prevent this issue, make sure that the ASA certificate is properly configured. The CN value in the certificate must match the name of the ASA server in the VPN client profile. - If there is another device on the network before the ASA that responds to the client's attempt to contact an ASA by blocking HTTPS access to the ASA, then the AnyConnect client will think it is in a captive portal environment. This situation can occur when a user is on an internal network and connects through a firewall in order to connect to the ASA.
If you must restrict access to the ASA from inside the corporation, configure your firewall such that HTTP and HTTPS traffic to the ASA's address does not return an HTTP status. HTTP/HTTPS access to the ASA should either be allowed or completely blocked (also known as black-holed) in order to ensure that HTTP/HTTPS requests sent to the ASA will not return an unexpected response.
Cisco Anyconnect Always On Vpn Android
AnyConnect Behavior
This section describes how the AnyConnect behaves.
- AnyConnect tries an HTTPS probe to the Fully Qualified Domain Name (FQDN) defined in the XML profile.
- If there is a certificate error (not trusted/wrong FQDN), then AnyConnect tries an HTTP probe to the FQDN defined in the XML profile. If there is any other response than an HTTP 302, then it considers itself to be behind a captive portal.
Captive Portal Incorrectly Detected with IKEV2
When you attempt an Internet Key Exchange Version 2 (IKEv2) connection to an ASA with SSL authentication disabled that runs the Adaptive Security Device Manager (ASDM) portal on port 443, the HTTPS probe performed for captive portal detection results in a redirect to the ASDM portal (/admin/public/index.html). Since this is not expected by the client, it looks like a captive portal redirect, and the connection attempt is prevented since it seems that captive portal remediation is required.
Workarounds
If you encounter this issue, here are some workarounds:
- Remove HTTP commands on that interface so that the ASA will not listen to HTTP connections on the interface.
- Remove the SSL trustpoint on the interface.
- Enable IKEV2 client-services.
- Enable WebVPN on the interface.
This issue is resolved by Cisco bug ID CSCud17825 in Version 3.1(3103).
Cisco Anyconnect Always On Vpn
Caution: The same problem exists for Cisco IOS® routers. If ip http server is enabled on Cisco IOS, which is required if the same box is used as the PKI Server, AnyConnect falsely detects captive portal. The workaround is to use ip http access-class in order to stop responses to AnyConnect HTTP requests, instead of requesting authentication.
How To Configure Cisco SSL VPN AnyConnect Secure Mobility ...
Disable the Captive Portal Feature
Cisco Anyconnect Windows Always On Vpn
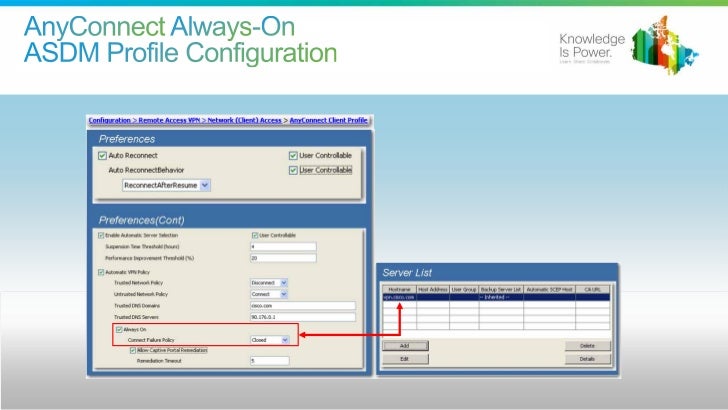
It is possible to disable the captive portal feature in AnyConnect client version 4.2.00096 and later (see Cisco bug ID CSCud97386). The administrator can determine if the option should be user configurable or disabled. This option is available under the Preferences (Part 1) section in the profile editor. The administrator can choose Disable Captive Portal Detection or User Controllable as shown in this profile editor snapshot:
If User controllable is checked, the checkbox appears on the Preferences tab of the AnyConnect Secure Mobility Client UI as shown here:
